搜索结果: 1-15 共查到“injection”相关记录245条 . 查询时间(0.109 秒)

Engineers develop precision injection system for plants(图)
Engineers precision injection system plants
2020/5/9
While the human world is reeling from one pandemic, ongoing epidemics are affecting crops and putting global food production at risk. Oranges, olives and bananas are under threat in many areas due to ...

中国地质大学科学技术发展院朱棋(博士研究生),文章*,等,环境学院. Journal of Hydrology (2019), Microbial effects on hydraulic conductivity estimation by single-well injection tests in a petroleum-contaminated aquifer(图)
有机物污染;注水试验;微生物生长
2021/10/15
近日,国际著名期刊《Journal of Hydrology》刊发了中国地质大学环境学院文章教授团队的最新研究成果——“Microbial effects on hydraulic conductivity estimation by single-well injection tests in a petroleum-contaminated aquifer”。该文第一作者为环境学院博士研究生朱...
A Fast Characterization Method for Optical Fault Injection
Physical attacks Fault injection Fast space characterization
2019/7/26
Semi-invasive fault injection attacks, such as optical fault injection, are powerful techniques well-known by attackers and secure embedded system designers. When performing such attacks, the selectio...
Experimental Evaluation of Deep Neural Network Resistance Against Fault Injection Attacks
fault attack neural network deep learning
2019/5/13
Deep learning is becoming a basis of decision making systems in many application domains, such as autonomous vehicles, health systems, etc., where the risk of misclassification can lead to serious con...
Practical Fault Injection Attacks on SPHINCS
SPHINCS hash-based signature voltage glitching
2018/7/16
The majority of currently deployed cryptographic public-key schemes are at risk of becoming insecure once large scale quantum computers become practical. Therefore, substitutes resistant to quantum at...
Template-based Fault Injection Analysis of Block Ciphers
Template Attacks Fault Injection Fault Intensity
2018/1/19
We present the first template-based fault injection analysis of FPGA-based block cipher implementations. While template attacks have been a popular form of side-channel analysis in the cryptographic l...
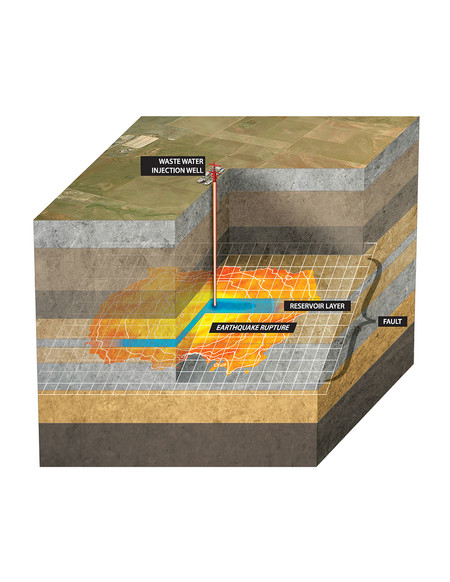
In work that offers insight into the magnitude of the hazards posed by earthquake faults in general, seismologists have developed a model to determine the size of an earthquake that could be triggered...
File-injection Attack and Forward Security for Order-revealing Encryption
Order-revealing Encryption Order-preserving Encryption File-injection Attack
2017/11/13
Order-preserving encryption (OPE) and order-revealing encryption (ORE) are among the core ingredients for encrypted database (EDB) systems as secure cloud storage. In this work, we study the leakage o...
A numerical simulation study of CO 2 injection for enhancing hydrocarbon recovery and sequestration in liquid-rich shales
CO2 EOR Tight formations Experimental design Response surface modeling Recovery of shale liquid CO2 sequestration
2018/4/2
Less than 10% of oil is usually recovered from liquid-rich shales and this leaves much room for improvement, while water injection into shale formation is virtually impossible because of the extremely...
Extending Glitch-Free Multiparty Protocols to Resist Fault Injection Attacks
secret sharing AES fault attacks
2017/3/27
Side channel analysis and fault attacks are two powerful methods to analyze and break cryptographic implementations. Recently, secure multiparty computation has been applied to prevent side channel at...
Dynamics of fluid and heat flow in a CO2-based injection-production geothermal system
Binary system CO2-water displacement Heterogeneity Preferential flow
2018/3/23
CO2 is now considered as a novel heat transmission fluid to extract geothermal energy. It can be used for both energy exploitation and CO2 geological sequestration. Here, a 3-D, “two-spot” pattern wel...
Inference and Record-Injection Attacks on Searchable Encrypted Relational Databases
searchable symmetric encryption inference attacks complexity theory
2017/2/20
We point out the risks of providing security to relational databases via searchable encryption schemes by mounting a novel inference attack exploiting the structure of relational databases together wi...
Causing a device to incorrectly execute an instruction or store faulty data is well-known strategy for attacking cryptographic implementations on embedded systems. One technique to generate such fault...
Secure Channel Injection and Anonymous Proofs of Account Ownership
privacy anonymity zero knowledge
2016/12/8
We introduce secure channel injection (SCI) protocols, which allow one party to insert a private message into another party's encrypted communications. We construct an efficient SCI protocol for commu...
Mistakes Are Proof That You Are Trying: On Verifying Software Encoding Schemes' Resistance to Fault Injection Attacks
software encoding schemes formal code analysis fault injection attacks
2016/12/8
Software encoding countermeasures are becoming increasingly popular among researchers proposing code-level prevention against data-dependent leakage allowing an attacker to mount a side-channel attack...

